JILT 1998 (2) - Derrick Glass et al.
A Software Asset Management (SAM) Methodology
AbstractSoftware piracy is the practice of copying and using a software product without the permission of its owner or developer. This practice is illegal because it is copyright infringement. The effects of software piracy are substantial and there is evidence that academia ranks as one of the worst abusers. If the validity of such a statement is true it is then necessary to understand why software usage within academia is inadequately controlled. Following a literature review of software asset management, with particular emphasis on software licensing, a survey of software administration within UK Higher Education Institutions, with a separate additional survey focusing on The University of Ulster, it is suggested that the key to gaining and retaining control of software assets is in unifying three processes - the software end user education process, the software administration process and the software audit process. This paper proposes the required unification by means of a Software Asset Management (SAM) Methodology. In this structured methodology the processes are represented as phases. Each phase is broken down into stages with supporting documentation. A stage can be decomposed down to the level of inputs, actions and deliverables. The incorporation of emerging technologies into a toolset for SAM is also considered and shown to be practicable.
This is a Refereed Article published on 30 June 1998. Citation: Glass D et al, 'A Software Asset Management (SAM) Methodology', 1998 (2) The Journal of Information, Law and Technology (JILT). <http://elj.warwick.ac.uk/jilt/itpract/98_2glas/>. New citation as at 1/1/04: <http://www2.warwick.ac.uk/fac/soc/law/elj/jilt/1998_2/glass/>. 1. IntroductionSoftware piracy is the practice of copying and using a software product without the permission of its owner or developer. It is a growing problem and becoming a prime concern within IT circles. Academia also has a major problem with the amount of illegal software in use. It is reported that academia rank as one of the worst offenders of the software copyright law ( Crow 1989 ). If the validity of such a statement is true it is then necessary to understand why software usage within academia is inadequately controlled. This understanding can be used to formulate a workable solution to alleviate the problem. To understand the underlying origins of the problem, four key areas of investigation were undertaken:
These areas of investigation indicated that the perceived weaknesses and therefore the successful resolutions may be found in three different yet interrelated processes: software end user education, software administration and software audit. These processes provide the foundation for developing the integrated Software Asset Management (SAM) Methodology. They are the main phases of the methodology. Each phase is broken down into stages with supporting documentation. A stage can be decomposed down to the level of inputs, actions and deliverables. This level of detail is not the subject of this paper. The first iteration of the SAM Methodology underwent a rigorous evaluation. This was carried out by thirteen software co-ordinators from the University of Ulster. The evaluators felt that overall the SAM Methodology was sound, well set out and easy to follow. As a result of the evaluation, the prototype was revised to improve the embedded control procedures and to make its implementation more responsive to the specialist requirements of staff end user. This revised version of SAM is presented in this paper. The paper also considers how to incorporate a toolset, derived from emerging technologies, into the SAM Methodology. 2. Current Issues in Software Asset ManagementSoftware Piracy is the practice of copying and using a software product without the express permission of its owner. This practice is illegal because it is an infringement of copyright ( Athey et. al.1994 ; Dakin 1995 ; Malhotra 1994(a); Malhotra 1994(b); Schramm et al.1995 ; Zanger et al.1992 ). The trend towards downsizing, that started in the early 1980's with the rapid development and the subsequent proliferation of microcomputers, has been closely associated with the unfortunate parallel growth of Software Piracy as a major wrong doing within IT circles ( Spikes Cavell Report 1995 ; Schramm et al.1995 ). In 1994 the Federation Against Software Theft (FAST) surveyed 600 senior UK directors about software theft. They found that whilst eighty six per cent of the respondents were aware of the pertinent issues, forty six per cent believed that software copying was prevalent within their organisation. Sixty five per cent stated ease of copying as the explanation for this. Software inventories were already maintained by eighty two per cent of the respondents. Sixty per cent had already implemented a centralised software purchasing and distribution policy as part of a move towards better management of software. Academia also has a major problem with the amount of illegal software in use ( Im J et al. 1991 ; Wickham M et al.1992 ; Crow 1989 ) stated that ' the effects of software 'piracy' are enormous and insidious, and academia ranks as one of the worst abusers .'. Karon (1986) surmised that ' software piracy is a bigger problem in the academic community than in the business community, largely due to a lack of vigorous enforcement of the copyright law by academic officials.' The amount of illegal software in current use world-wide is large. In 1990 the estimated world market for software was $43 billion ( Malhotra 1994(b)). In the same year it was estimated that world-wide losses due to software piracy were $10 to $12 billion. In Europe it is estimated that illegal software is worth $4.6 billion. Software piracy is greatest in the Asian software market place; 90% of the software in use in Japan is illegal ( Malhotra 1994(b); Spikes Cavell 1995 ). In 1990 the US software companies lost $758 million in software piracy in Taiwan and $400 million to China. The corresponding estimates of illegal software use within the UK are 54%. The U.S. has the best legal record - approximately 33% of the software being illegal. Factors contributing towards software piracy and suggested solutions are summarised in Table 1. Table 1: Factors contributing towards and contributions towards tackling software piracy
As a generalisation, software infringement occurs either through the misappropriation of the physical media ('hard' theft) or by copying of the software from one storage device to another ('soft' theft). Various categories of software pirates include:
3. Software Protection MethodsThree forms of control mechanisms can be used to create the incentives for obtaining the software legally and penalties or disincentives for using the software illegally ( Malhotra 1994b ). A technology based control mechanism uses an encryption process or other protective measures to protect the software. The most common approaches are: making distribution disks copy resistant, access locks, hardcoded numbers in computer memory, software resident inside a ROM chip and copy protection security devices. This form of control will prevent accidental use of unauthorised software by the end user. It will not prevent those who make it their business to pirate software. Increasingly many software manufacturers are looking to legal control mechanisms . Software licence agreements and copyright law are being used to prevent software piracy ( Crow 1989 ; Malhotra 1994(a) and 1994(b); Zanger et al 1992 ; Bundy A et al.1994 ). Of the two legal control mechanisms copyright law is the more important. It covers all software automatically. These control mechanisms do not prevent a user from inadvertently or intentionally copying the unauthorised software. The power of these mechanisms is in the legal remedies available to the software suppliers against the software pirates. Software publishers and suppliers are also using various marketing control mechanisms to reduce the incidence level of software piracy. These include for example, volume discounting, site licensing, strong focus on customer support, etc. With the software industry losing billions of dollars each year due to software piracy several organisations have been sponsored by the major software publishers to 'police' the software industry. The best known of these organisations are: the Software Publishers Association (SPA), the Business Software Alliance (BSA) and the Federation Against Software Theft (FAST). Both SPA and BSA have an international remit and impact on the software industry. FAST is the organisation with which the UK software industry would be most familiar. These software guardians have similar mission statements: ' to eradicate software piracy by educating personal computer users about the copyright law and providing them with the tools necessary to comply with the copyright law and to execute a legal campaign to fight software piracy '. These organisations will undertake software audits, on behalf of the software publishing community, of organisations suspected of software piracy. Many of the larger software producers are also taking more direct steps to protect their software interests. More recent software licence agreements, for example CHEST site licences ( see Table 3 ), contain a clause that gives the software producer the right to conduct a software audit within the subscribing software user organisation. 4. An Overview of a University's Software PortfolioTo avoid any potential for misinterpretation it is important to define some common terminology that will be used in this paper. A site licence provides for the distribution for a single agreed fee of a software product x throughout the institution as required by the end users. The charge is not affected by the end user uptake. An incremental site licence is similar to a site licence but is directly affected by the end user requirements. Licence charging is set in terms of the software licence uptake 'bands'. Control refers to the mechanisms imposed by the vendor to control the software usage such as the requirement for a software licence code. Within a university at least eight categories of software licence, by purchase method and agreement, may be identified (Table 2). Table 2: Categories of software licence by purchase method/agreement
An alternative means of presentation is to categorise software licences by supplier type (Table 3). Table 3: Software Portfolio Categorised By Supplier Type
5. Software Administration within UK Higher Educational InstitutionsThis section presents the findings of two studies designed to survey current software administration and control practices within the UK Higher Education Community. 5.1 The Durham StudyA questionnaire was used to obtain an overview of how the Software Audit Process was administered within the IT departments of the Higher Education Community in the UK. The sample was drawn from attendees at a Universities and Colleges Information Systems Association (UCISA) Software Asset Management Seminar, Durham 1996. Sixty one academic institutions were represented. Twenty three useable questionnaires were returned giving a return rate of thirty eight per cent. The results indicate that Computer Services Departments within universities play a major role both in the procurement of hardware and software and in the provision of ongoing IT services. A close working relationship with user Faculties is also evident. Diversity of software portfolios is large within Institutions. Overall investment in micro-computing is correspondingly high. Most respondents (91%) stated that software licences were recorded centrally - thirty nine per cent within Computer Services, seventeen per cent within Faculties and thirty nine per cent centrally through both areas. The way in which the users are informed about the Software Code of Practice varies within and between Institutions. It also varies between staff and student users ( Table 4 ). A more standardised approach to end-user education is of strategic importance. Only thirteen per cent of respondents currently use a software audit tool. Sixty five per cent are in the evaluation or inquiry stage and twenty two per cent have no current interest in such a tool. 5. 2 The University of Ulster StudyThe second study assessed in detail how the Software Audit Process was administered within the Faculties and Administration Departments of the University of Ulster. The same questionnaire was used as in the Durham study (with appropriate questions redrafted to ensure that the respondents answered on behalf of their respective areas as opposed to institution level). The respondents were selected based on their responsibility for the procurement and administration of the software within their areas. The survey was conducted by means of interviews to ensure a one hundred per cent response rate from a small sample (thirteen). It also helps to clarify respondents' questions and to elicit and record any additional information. The results of this second study prove the view that the Computer Services department have a pivotal role in both the procurement and administration of the software. The diversity of the software portfolio has been confirmed by the responses made. In addition the software portfolio of a Faculty is specific to the disciplines of the Faculties. All areas include Microsoft products within their software portfolios. Finally, all respondents report that supplier pre-installed operating systems are the norm. All respondents stated that software licences were held centrally. Closer examination of the responses indicates a breakdown of thirty eight per cent within the Computer Services department, twenty three per cent within the Faculty, and thirty nine per cent centrally through both areas. The method used for recording software licence details varies and encompasses databases or spreadsheets (sixty two per cent) and paper filing systems (thirty one per cent). Currently no standardisation of method exists or has been proposed. Current interest in software auditing tools is limited apart from Computer Services. Half of the Faculties and the Administration Departments stated that they were either at an evaluation or inquiry stage. These responses were made based on a pilot study of a software audit tool organised by Computer Services in 1995. The way in which the end users (staff and students) within the University of Ulster are advised as to the Correct Software Code of Conduct is neither standardised nor well defined ( Table 4 ). The most popular method for informing students is to rely on notices prominently displayed within the micro-computing laboratories. Whilst at first sight this may appear sound it is a passive approach that cannot be relied upon. With staff, the most popular approach is to advise them by means of periodic memos. However, only fifty four per cent of respondents said that they used this method. As a result, the University of Ulster cannot be confident that all end users have been advised of the Correct Code of Software Conduct. Table 4: Approaches Taken to Inform Staff and Students of Software Code of Conduct
The findings of the two studies suggest that software administration and control within the UK Higher Education Community is not satisfactory. These weaknesses and therefore their successful resolution may be found in three distinct but interrelated processes:
6. The Software Asset Management (SAM) MethodologyThe SAM Methodology consists of three phases: software end user education, software administration and software audit. The phases are broken down into a number of stages. Each stage is broken down to the level of objectives, inputs, actions and deliverables. (This level of detail is not the subject of this paper.) 6.1 Phase I - Software End User EducationThe main concern of the first phase is the education of all potential end users (staff and students) as to the correct software code of conduct. The objective of this phase is ' to ensure that all end users are fully aware of the institution Software Code of Conduct and to record acceptance of this code by the end user '. This phase consists of four stages (Fig. 1.) Figure 1: SAM Methodology - Phase 1 - Software End User Education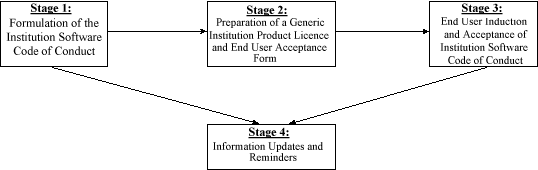
In Stage 1 a software code of conduct is formulated and published for the institution. This software code of conduct should:
The software code of conduct needs to be endorsed by a senior officer of the institution (the Vice Chancellor or equivalent). This could be a signed memorandum stressing the legal implications of the software copyright law and the potential consequences of unauthorised software copying. It should outline the internal disciplinary action that will be taken against offenders. Unlike the other stages the first stage is not iterative. The objective of Stage 2 is to prepare a standard pre-numbered form for recording product licence agreements within the institution. Educational materials are produced that may be used:
The main concern of Stage 3 is preparing a software education package (SEP). This package will include the institution code of software practice. It will be used during staff induction and student enrolment. Stage 3 also involves recording acceptance of this code by the end user. The objective of Stage 4 is to identify mechanisms for providing end users with information updates and reminders pertaining to usage of software products. 6.2 Phase 2 - Software AdministrationThe software administration process is the sequence of events that occurs in the provision of the end user with the requested software. The overall objective of this phase is ' to provide a method for delivering the requested software products to end users which is fully compliant with: the Software Copyright Law, the individual software product licence and the institution software code of conduct and in such a way as to establish a verifiable audit trail of product acquisition and distribution to the end user .' The SAM Methodology recommends using software co-ordinators to facilitate the provision of the software product to the end users (Fig. 2). Two types of co-ordinators are required: a university software co-ordinator (USC) and a software co-ordinator (SC) within each faculty and each of the larger non faculties administrative areas. Figure 2: Software Administration Process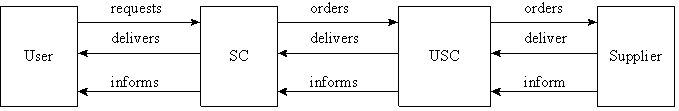
The role of the university software co-ordinator is:
The role of the Faculty or Departmental software co-ordinator is:
The end users, within an academic environment, may be categorised as being staff or students. Differences between these groups suggest that the different way in which their product requests are attended to warrant a separate sub-phase for each - Phase 2a (servicing the staff end users) and Phase 2b (servicing the student end users). 6.2.1 Phase 2a - Servicing Staff End UsersThis sub-phase consists of two pre-stages and five stages proper. Pre-stage 1 transfers the administration of the department(s) software budget to the relevant software co-ordinator. This has the positive benefits of stream lining the authorisation process. It adds an additional security feature to the process in that the head of department's authorising signature to spend can no longer be forged. Figure 3: SAM Methodology - Phase 2 - Software AdministrationPhase 2a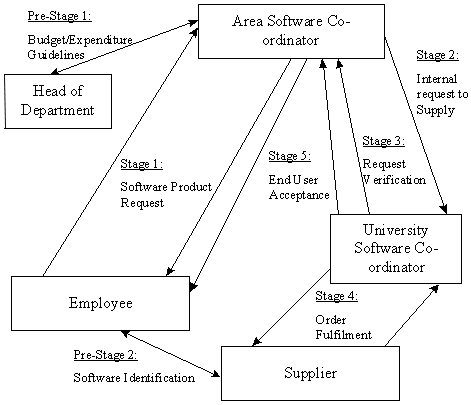
Phase 2b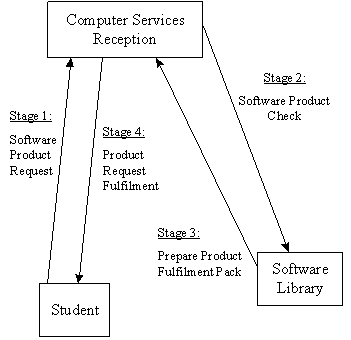
The main objective of Pre-stage 2 is to allow the end users to investigate the identification and sourcing of the software product. The main deliverable is a pre-numbered triplicate Supplier Contact Sheet. The top copy is sent to the end user originating the request, second copy to the software co-ordinator and third copy to the university software co-ordinator. The objective of Stage 1 is to assist the end users in making a software product request. End users are required to sign the pro-forma licence form at this stage. This results in the product being delivered only to those who have signed the pro-forma licence. The main document used is a pre-numbered duplicate Staff End User Product Request Form. This is cross-referenced to the Supplier Contact Sheet (if required) and the end user signed pro-forma licence (top copy to the software co-ordinator, bottom copy to the end user). The aim of Stage 2 is to assist the software co-ordinator to make a product request to the university software co-ordinator. A triplicate pre-numbered Software Product Request Form is used. The top copy is sent to the software co-ordinator, second and third copy to the university software co-ordinator. This form is cross-referenced to the Supplier Contact Sheet (when applicable), the signed pro-forma licence and the Staff Product Request Form. The task for verifying the software request is outlined in Stage 3. The university software co-ordinator checks that the Staff Product Request Forms are properly completed. Acceptance is communicated back to the software co-ordinator originating the request. The third or bottom copy of the Staff Product Request Form is forwarded to Finance Department to obtain inter-departmental transfer of funds. The main task in Stage 4 is the preparation of the Product Fulfilment Package (PFP). This is prepared by the university software co-ordinator after the ordered product(s) has arrived from the supplier. A pre-numbered quadruple Product Acceptance Form is used to complete the audit trail between the university software co-ordinator, the software co-ordinator and the end user. This is initially completed by the university software co-ordinator. Parts 2, 3 and 4 of this form are included in the PFP. The PFP is then sent to the software co-ordinator originating the request. Depending on what has been requested and by which category of end user, the PFP will contain all, or some of the following items:
The main objective of Stage 5 is to record acceptance of the Product Fulfilment Package by the end user. Once the software product has been successfully installed, the Product Acceptance Form is signed by both the end-user and the software co-ordinator. Part 2 of the form is retained by the end user, part 3 by the software co-ordinator and part 4 is returned to the university software co-ordinator. 6.2.2 Phase 2b - Servicing Student End UsersThis sub-phase consists of three stages. The objective of Stage 1 is to provide a mechanism for the student end users to make the software product request. Students complete part 1 of the Student Product Request Form and then pass the form to the reception staff at Computer Services. During stage 2 the identity of the end user as a member of the institution is verified by the reception staff. The main deliverables from this stage will be the Student Product Request Form with details of the PFP to be prepared. Students are also advised when to return for collection of the PFP. The main objectives of stage 3 are to prepare the PFP and record acceptance of the PFP by the end user. There are elements in common to both sub-phases of this Phase - a Product Request Form designed for each user type and a Product Fulfilment Package (PFP). 6.3 Phase 3 - Software AuditSoftware is a business asset and as such has associated costs and benefits to the organisation. Few organisations will know the total value or cost of their software investment or have any means in place to track it. The objective of this Phase of the SAM Methodology is ' to measure the effectiveness and efficiency of the institution's software education and administration processes .' Phase 3 of The SAM Methodology consists of four stages (Fig. 4). The main objective of Stage 1 is to produce a detailed audit plan. The first task is to clearly define the objectives of the IT audit and the need for it. The next task is to formalise the members of the audit team and then decide what information to obtain from the audit. Having reached decisions on what to look for and where to look; the audit project timescales are planned. Stage 2 outlines how to perform the audit according to the project plan derived in Stage 1. Figure 4: SAM Methodology - Phase 3 - Software Audit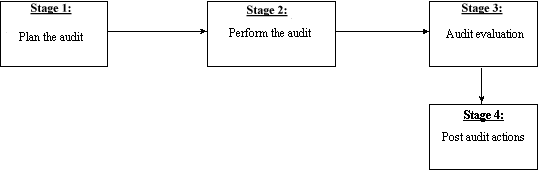
Having used a considerable amount of time and resources in the planning and carrying out of the IT audit the next stage (Stage 3) is to perform an audit evaluation. This stage is concerned with evaluating:
The licence reconciliation process is performed during Stage 3. The main task is to reconcile the identified installed software base against the internally held records of the original licences and the purchase records. If the audit detects and identifies more software than can be reconciled, then this is a clear indication of illegal software usage. Corrective action must be taken immediately. This is the main concern of stage 4 (Post audit actions). The main tasks performed during this stage are:
Stages 1, 2 and 3 are specifically concerned with:
The final action arising out of the software audit phase of The SAM Methodology is to revise the Methodology as a direct consequence of Phase 3, Stage 4. 7. Evaluation of The Software Asset Management MethodologyThe first iteration of the SAM Methodology underwent a rigorous walk through evaluation. This was carried out by thirteen software co-ordinators from the University of Ulster. The evaluators felt that overall the SAM Methodology was sound, well set out and easy to follow. As a result of the evaluation, the prototype was revised to improve the embedded control procedures and to make its implementation more responsive to the specialist requirements of the staff end user. This revised version of SAM is presented in this paper. The other main issues, outside the scope of this paper, resulting from the evaluation were:
8. A Toolset For SAMTo improve the effectiveness of the SAM methodology we need to consider the selection of an appropriate electronic toolset. As shown in table 5 there are two options for the make up and acquisition of a suitable toolset. The first option is to acquire each component of the toolset as an individual item. For example, access to the WWW, a database management system, etc. In this option product integration is the responsibility of the user. The second option is to buy an integrated toolset, for example, an enterprise management system. Table 5: Possible Toolsets For SAM
The emergence of sophisticated toolsets does not negate the need for having a methodology. The two are complementary. The main strength of SAM is that it addresses the requirements for making sure that all end users understand their obligations in using software products as defined within the software copyright law. It also shows how to successfully gain control over the process of software asset management and demonstrate that this has been achieved. 9. ConclusionThis paper has examined the potential weaknesses contributing to the incidence of unauthorised software within the Higher Education Community. These weaknesses provided the framework for developing the Software Asset Management methodology. Three discrete processes were 're-engineered' to form the three phases of the methodology. Each phase has a specific objective and a direct link with the other two phases. The three phases are subdivided into stages (see Table 6). Each stage has a defined set of objectives, inputs, actions and deliverables. Successful implementation of the stages within each phase combines to achieve the stated phase objective. Table 6: Phases and Stages of the SAM Methodology
Software piracy is a serious wrong doing. It is therefore necessary for organisations to have in place a set of procedures for tracking and controlling the use of software. The Software Asset Management Methodology provides a mechanism for implementing these procedures. There is also potential for improving the methodology by including a suitable toolset (Figure 5). Figure 5: The SAM Methodology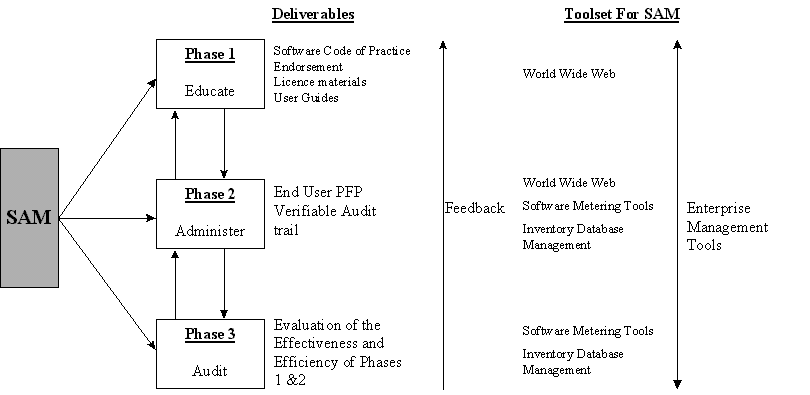
ReferencesAthey S and Plotnicki J (1994) 'Would the Software Police Find Your Company Guilty?' Journal System Management (USA) Vol. 45, No. 10, pp 32-38. Bundy A and MacQueen H (1994) 'The new software copyright law', Computing Journal (UK) Vol. 37, No. 2, pp 79-82. Crow G B (1989) 'Defining educational policy on software usage in light of copyright law', SIGCSB Bulletin Vol. 21, No. 1, pp 47-51. Dakin K J (1995) 'Do You Know What Your License Allows?' IEEE Software (USA) Vol. 12, No. 3, pp 82-83. Im J H and Van Epps P D (1991) 'Software Piracy and Software Security in Business Schools: An Ethical Perspective', Database Vol. 22 Part 3, pp l5-21. Malhotra J (1994a) 'Controlling Copyright Infringements of Intellectual Property: The Case of Computer Software - Part One', Journal System Management (USA) Vol. 45, No. 6, pp 32-35. Malhotra J (1994b) 'Controlling Copyright Infringements of Intellectual Property: The Case of Computer Software - Part two', Journal System Management (USA) Vol. 45, No. 7, pp l2-17. Schramm R M, James M L and Moses D R (1995) 'The legal Case Against Software Piracy', Off. Syst. Res. J. (USA) Vol. 13, No. 1, pp 29-34. Spikes Cavell & Co. Ltd. (1995) Software Theft in the UK . (Microsoft commissioned report). l03-104. Zanger L M, McBride, Baker and Coles (1992) 'Copying PC Software: When is it Legal?', IEEE Software (USA) Vol. 9, No. 5, pp Wickham M, Polotnicki J and Athey, S (1992) 'A survey of Faculty attitudes towards personal computer software copying' Journal Computing Information System. (USA) Vol. 32, No. 4, pp 47-52. |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
